Internet scams refer to fraudulent activities conducted online with the intent to deceive and exploit individuals or organizations for financial gain. These deceptive practices take advantage of the vast connectivity and anonymity provided by the internet. Dating back to the early days of the World Wide Web in the 1990s, scams have evolved in complexity and sophistication over the years. One prominent form of internet scam is phishing, where cybercriminals attempt to trick individuals into divulging sensitive information, such as passwords or credit card details, by posing as trustworthy entities. The late 1990s and early 2000s witnessed the rise of email scams, often known as “419 scams” or “Nigerian Prince scams,” where fraudsters claimed to share a large sum of money in exchange for a small upfront payment. As technology advanced, so did the methods of online deception. In the 2010s, ransomware emerged as a significant threat, encrypting victims’ data and demanding payment for its release. Additionally, the proliferation of social media platforms provided new avenues for scams, including fake profiles, romance scams, and investment fraud. The battle against internet scams remains ongoing, with law enforcement, cybersecurity experts, and individuals working together to raise awareness and implement preventive measures to curb the impact of these digital deceptions.
Phishing Scams
Phishing scams have become an increasingly prevalent and sophisticated form of cybercrime, posing significant threats to individuals, businesses, and organizations worldwide. The term “phishing” originates from the analogy of fishing, where cybercriminals attempt to lure unsuspecting individuals into providing sensitive information, such as usernames, passwords, and financial details. This form of social engineering relies on deception and manipulation to exploit human psychology for malicious purposes.
Definition: Phishing is a cyber attack technique where attackers masquerade as trustworthy entities to deceive individuals into divulging sensitive information. These deceptive attempts often occur through various communication channels, such as emails, text messages, or fake websites, with the intention of stealing valuable data for fraudulent activities.
Types of Phishing:
- Email Phishing: This is the most common form of phishing, where attackers send fraudulent emails appearing to be from reputable sources, such as banks, government agencies, or legitimate businesses. These emails typically contain urgent messages, prompting recipients to click on malicious links or provide sensitive information.
- Spear Phishing: In spear phishing, attackers target specific individuals or organizations, tailoring their deceptive messages based on detailed information about the target. This customization increases the likelihood of success, as the messages seem more legitimate and personalized.
- Smishing (SMS Phishing): Smishing involves phishing attacks conducted through text messages. Cybercriminals send SMS messages containing links or prompts that, when clicked, lead to malicious websites or trick individuals into revealing sensitive information.
- Vishing (Voice Phishing): Vishing utilizes voice communication, where attackers use phone calls to impersonate trusted entities, such as banks or government agencies. They manipulate victims into disclosing personal information or performing actions that compromise security.
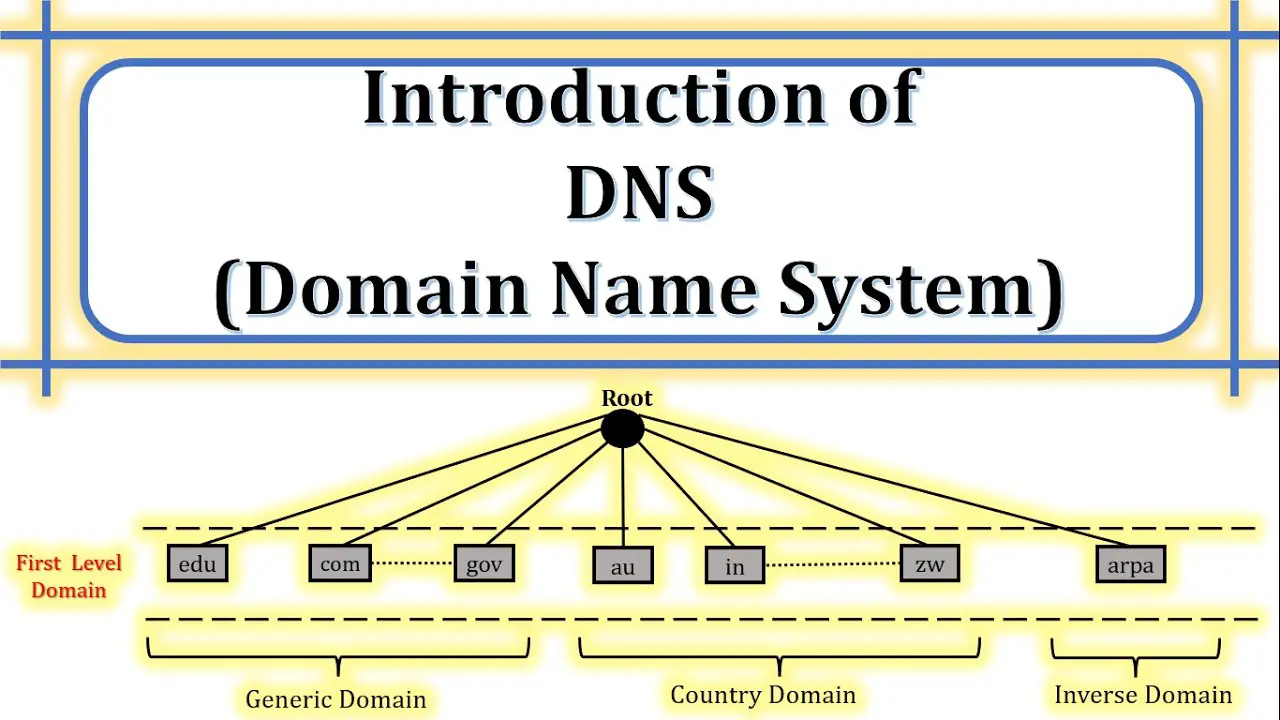
- Pharming: Pharming involves redirecting website traffic to fraudulent sites without users’ knowledge. Attackers exploit vulnerabilities in the domain name system (DNS) or compromise routers to redirect users to malicious websites, where they unknowingly provide sensitive information.
Examples:
- Email Spoofing: Attackers may send emails that appear to be from a legitimate source, such as a bank or a popular online service, requesting users to verify their account information by clicking on a link. The link, however, leads to a fake website designed to capture login credentials.
- CEO Fraud: In a spear phishing scenario, cybercriminals may impersonate high-ranking executives within an organization. They send emails to employees, often in the finance or human resources departments, requesting urgent wire transfers or sensitive employee information.
- Fake Tech Support Calls: Vishing scams may involve fraudulent phone calls from individuals posing as technical support representatives. They claim to have identified issues with the victim’s computer or account, persuading them to provide remote access or disclose personal information.
- Phishing via Social Media: Cybercriminals leverage social media platforms to create fake profiles or pages resembling legitimate organizations. They use these profiles to send messages or post links, tricking users into providing sensitive information or downloading malware.
Phishing scams continue to evolve and adapt to technological advancements, making it crucial for individuals and organizations to stay vigilant. Recognizing the signs of phishing attempts, employing robust security measures, and educating users about the dangers of these scams are essential steps in mitigating the risks associated with phishing. As technology progresses, so do the tactics of cybercriminals, underscoring the importance of ongoing awareness and cybersecurity measures to protect against these pervasive threats.
Online Shopping Scams
Online shopping has become an integral part of our lives, providing convenience and a wide array of choices. However, with the rise of e-commerce, online shopping scams have also proliferated, posing significant threats to consumers. This article explores three common types of online shopping scams – Bogus Websites, Non-Delivery of Goods, and Counterfeit Products – with examples and dates to highlight the evolving nature of these fraudulent activities.
1. Bogus Websites: Bogus websites are created to deceive consumers into thinking they are legitimate online stores. These fraudulent sites often mimic the design and layout of well-known e-commerce platforms, making it challenging for unsuspecting shoppers to discern the difference. One infamous example is the case of the website ‘ElectroniksZone.com,’ which claimed to offer heavily discounted electronics. This site operated briefly in early 2019 before being exposed as a scam. Customers reported receiving counterfeit or non-functional products, while others never received any items despite making payments.
2. Non-Delivery of Goods: In this type of scam, customers place orders and make payments, but the purchased items are never delivered. An illustrative case involves the website ‘FashionFiesta.com,’ which emerged in the summer of 2020. Promising trendy clothing at unbelievable prices, the site attracted numerous customers. However, as complaints started pouring in, it became evident that the site was a sham. Many customers never received their orders, and attempts to contact the company proved futile. This incident highlights the importance of researching online sellers and reading reviews before making purchases.
3. Counterfeit Products: Counterfeit products are fake replicas of genuine items, often sold at seemingly attractive prices. Scammers take advantage of the demand for popular brands to lure unsuspecting shoppers. An example is the ‘LuxuryDealz.store,’ which emerged in late 2021, claiming to offer high-end fashion brands at significant discounts. Customers who fell victim to this scam received poorly made imitations or, in some cases, no products at all. Counterfeit product scams exploit the trust consumers place in established brands, emphasizing the need for caution when encountering seemingly too-good-to-be-true deals.
As these examples demonstrate, online shopping scams continue to evolve, adapting to consumer behaviors and technological advancements. To protect themselves, consumers should adopt several preventive measures:
- Research the Seller: Before making a purchase, research the online store or seller. Look for reviews and ratings from other customers to gauge their legitimacy.
- Check Website Security: Ensure that the website has secure payment options. Look for “https://” in the URL and a padlock symbol in the address bar, indicating a secure connection.
- Be Skeptical of Unrealistic Deals: If a deal seems too good to be true, it probably is. Scammers often use extremely low prices to lure victims.
- Use Trusted Platforms: Stick to well-known and reputable online shopping platforms. They have robust security measures and policies in place to protect consumers.
- Verify Contact Information: Legitimate businesses provide valid contact information. Verify the seller’s address, phone number, and email before making a purchase.
By staying vigilant and adopting these precautions, consumers can reduce the risk of falling victim to online shopping scams. As the online landscape evolves, so must our awareness and protective measures to ensure a safe and secure online shopping experience.
Identity Theft
Identity theft is a pervasive and sophisticated form of cybercrime that involves the unauthorized acquisition and use of an individual’s personal information for fraudulent purposes. This malicious practice has evolved over the years, employing various techniques to exploit vulnerabilities and compromise the privacy and financial security of unsuspecting victims.
1. Techniques Used: Identity thieves employ a range of techniques to gather personal information, such as phishing, social engineering, and hacking. Phishing involves the use of deceptive emails or websites to trick individuals into providing sensitive information like passwords or credit card details. For example, in 2013, the Target data breach exposed 40 million credit and debit card accounts through a phishing attack on the company’s HVAC vendor. Social engineering relies on manipulating individuals into divulging confidential information. A common tactic is pretexting, where the thief creates a fabricated scenario to obtain personal details. In 2008, Sarah Palin’s Yahoo email account was compromised through social engineering when an attacker guessed her security questions and reset her password. Hacking involves exploiting vulnerabilities in computer systems to gain unauthorized access to databases containing personal information. The Equifax data breach in 2017, for instance, exposed the personal data of 147 million individuals, highlighting the impact of hacking on a massive scale.
2. Consequences: The consequences of identity theft can be devastating for victims. Financial losses, damaged credit scores, and emotional distress are just a few of the potential outcomes. Identity thieves often use stolen information to open fraudulent bank accounts, apply for credit cards, or make unauthorized purchases. Victims may find themselves facing debt, legal issues, and the arduous task of reclaiming their stolen identity. In addition to financial repercussions, identity theft can tarnish one’s reputation. The misuse of personal information can lead to false criminal accusations or tarnish a person’s professional standing. The emotional toll of dealing with the aftermath of identity theft, coupled with the time-consuming process of restoring one’s identity, can be overwhelming.
3. Prevention: While identity theft is a persistent threat, there are measures individuals can take to protect themselves.
- Strong Passwords and Two-Factor Authentication (2FA): Using complex passwords and implementing 2FA adds an extra layer of security, making it harder for attackers to gain unauthorized access.
- Regular Monitoring of Financial Statements: Periodically checking bank and credit card statements for any unauthorized transactions can help detect suspicious activity early on.
- Secure Wi-Fi Networks: Ensuring that home Wi-Fi networks are password-protected and using encryption protocols enhances overall cybersecurity.
- Educating Against Phishing: Being cautious of unsolicited emails, avoiding clicking on suspicious links, and verifying the authenticity of requests for personal information can prevent falling victim to phishing attacks.
- Credit Freezes: Placing a credit freeze on one’s accounts restricts access to personal information, preventing identity thieves from opening new accounts.
Identity theft remains a significant threat in the digital age, with attackers employing increasingly sophisticated techniques. Understanding these methods, recognizing the potential consequences, and implementing proactive prevention measures are crucial steps in safeguarding personal information. By staying informed and adopting best practices in cybersecurity, individuals can significantly reduce their risk of falling victim to identity theft.
Advance Fee Fraud
Advance Fee Fraud is a cunning and pervasive form of deception that preys on individuals’ eagerness for financial gain or lucrative opportunities. This fraudulent scheme typically involves a scammer convincing a victim to pay a fee upfront in the promise of receiving a larger sum of money or some form of valuable reward. It takes various forms, including lottery and prize scams, inheritance scams, and job opportunity scams, each with its unique set of tactics.
1. Lottery and Prize Scams: The Illusive Jackpot
Lottery and prize scams have been a prevalent form of Advance Fee Fraud for years, targeting individuals with the promise of a life-changing jackpot. Victims often receive emails or letters claiming they have won a lottery they never entered or a prize they never pursued. To claim their supposed windfall, victims are asked to pay upfront fees for processing, taxes, or other fabricated expenses. One infamous example dates back to 2018 when a widespread lottery scam circulated claiming individuals had won a massive cash prize from an international lottery. To claim their winnings, victims were instructed to wire a substantial sum as processing fees. Unfortunately, many fell victim to this ruse, losing not only their upfront payments but also their dreams of a nonexistent fortune.
2. Inheritance Scams: The Phantom Windfall
Inheritance scams play on the allure of unexpected wealth, often involving a scammer posing as a lawyer, government official, or distant relative. Victims receive communications informing them of an unclaimed inheritance from a long-lost relative or a wealthy individual with no apparent heirs. The catch, of course, is that the victim must pay fees to facilitate the release of the supposed inheritance. A notable case from 2019 involved an email scam where recipients were informed of a deceased relative with a vast fortune, waiting to be transferred to them. The victims were instructed to pay legal fees and taxes upfront. Sadly, many individuals, blinded by the prospect of newfound wealth, ended up losing substantial amounts to these fraudsters.
3. Job Opportunity Scams: False Promises of Employment
Job opportunity scams capitalize on the vulnerability of job seekers, promising lucrative positions with minimal effort. Scammers often pose as recruiters or employers, offering high-paying jobs or work-from-home opportunities. To secure the promised position, victims are required to pay fees for background checks, training materials, or other fictitious expenses. In 2020, reports surfaced about a widespread job opportunity scam targeting individuals seeking remote work during the COVID-19 pandemic. Victims were promised well-paying positions with flexible hours, but to start, they had to pay for training materials and administrative costs. As economic uncertainties loomed, many fell victim to this scam, losing money they could ill afford.
Advance Fee Fraud, manifested through lottery and prize scams, inheritance scams, and job opportunity scams, continues to exploit individuals globally. While the tactics may evolve, the core strategy remains the same: manipulating human desires for financial gain. Awareness and education are crucial in the fight against these scams, as individuals must remain vigilant to protect themselves from falling prey to the web of deception carefully woven by fraudsters.
Online Dating Scams
Online dating has become increasingly popular in recent years, providing individuals with the opportunity to connect and form relationships across geographical boundaries. However, this surge in online dating has also given rise to a darker side of the virtual realm – online dating scams. These scams take various forms, with romance scams and catfishing being two prevalent tactics employed by cybercriminals to exploit unsuspecting individuals.
1. Romance Scams:
Romance scams involve fraudsters creating fake online profiles to establish romantic relationships with the sole purpose of deceiving victims for financial gain. Typically, scammers build a connection with their targets over time, expressing love and affection to manipulate emotions. As the relationship deepens, they fabricate elaborate stories to evoke sympathy and convince victims to send money. One notable case occurred in 2018 when an individual, under the pseudonym “David,” targeted a woman on a popular dating site. Claiming to be a successful businessman working abroad, he gradually gained her trust. Eventually, he concocted a fictional emergency, requesting a substantial sum of money to resolve the supposed crisis. The victim, emotionally invested in the relationship, wired the funds only to discover later that “David” was a scammer.
2. Catfishing:
Catfishing is another form of online deception where individuals create fake personas, often using stolen photos, to establish relationships under false pretenses. These catfishers may engage in emotional manipulation, seeking attention, companionship, or even revenge. In extreme cases, catfishers may go to great lengths to maintain the deception, creating intricate webs of lies that can lead to devastating consequences for their victims. In 2017, a widely reported case involved a woman named Emma who believed she was in a long-distance relationship with a charming man named James. After months of online interaction and promises of a future together, Emma discovered that “James” was actually a catfisher using stolen photos and a fabricated identity. The emotional toll on Emma was substantial, highlighting the profound impact of catfishing on victims’ lives.
3. Warning Signs:
To protect oneself from falling victim to online dating scams, it is crucial to be aware of warning signs. These signs can include:
- Too Good to Be True: Be cautious if the person seems too perfect or their story is exceptionally dramatic.
- Unrealistic Photos: If the profile photos appear excessively polished or look like stock images, it could be a red flag.
- Quick Declarations of Love: Scammers often profess love rapidly to expedite their manipulation.
- Requests for Money: Never send money to someone you’ve only met online, especially if they request it under the guise of an emergency or unexpected situation.
- Reluctance to Meet in Person: If the person consistently avoids face-to-face meetings and offers excuses, be wary.
- Inconsistencies in Stories: Pay attention to any inconsistencies or contradictions in the information provided by the person.
Staying vigilant and skeptical, even in the realm of online romance, is crucial to avoiding falling prey to these scams. By educating oneself about the common tactics employed by scammers and being mindful of warning signs, individuals can navigate the online dating landscape more safely and protect themselves from potential emotional and financial harm.
Tech Support Scams
Tech support scams are a prevalent and malicious form of online fraud that preys on individuals’ lack of technical knowledge and fear of computer security threats. These scams typically involve deceptive tactics to trick unsuspecting users into believing their computers are infected with viruses or malware. Here, we’ll delve into three common methods employed by tech support scammers: cold calling, pop-up messages, and fake security software.
1. Cold Calling: One of the most traditional yet effective techniques employed by tech support scammers is cold calling. In this method, fraudsters call potential victims, often claiming to be representatives from well-known technology companies such as Microsoft or Apple. They inform the targets that their computers have been infected with viruses or are at risk of a security breach. To gain trust, scammers might use fake employee IDs and reference official-sounding information. An example of this occurred in 2018 when the Federal Trade Commission (FTC) issued a warning about a surge in tech support scams. These scammers were not only posing as reputable companies but also manipulating caller ID information to appear legitimate. The FTC advised users to be cautious when receiving unsolicited calls regarding computer security issues and to never provide remote access to their devices to unknown callers.
2. Pop-up Messages: Tech support scammers also deploy pop-up messages on websites, creating a sense of urgency and panic for users. These pop-ups often display alarming messages claiming that the user’s computer has been infected with a virus or that their personal information is at risk. The messages may include a phone number to call for immediate assistance. In 2019, a significant increase in pop-up tech support scams was reported. Cybercriminals exploited vulnerabilities in web browsers to deliver these deceptive pop-ups. Users were urged to call a specified number to resolve the purported issues, but in reality, they would be connected to fraudsters seeking to extract money or gain unauthorized access to their computers.
3. Fake Security Software: Scammers also create and distribute fake security software, commonly known as scareware or rogue security software. They often use aggressive marketing techniques, such as pop-ups or email campaigns, to convince users that their computers are infected. Victims are then prompted to download and install the fraudulent security software to purportedly fix the nonexistent issues. An example from 2017 involved a scam where fake Microsoft security products were being advertised. Users who fell for the scheme would be directed to websites resembling official Microsoft pages, encouraging them to purchase and download the bogus software. Microsoft, in response, issued warnings to users about the prevalence of such scams and advised them to rely on genuine security software from trusted sources.
Tech support scams continue to evolve, with scammers employing various tactics to exploit unsuspecting individuals. Cold calling, pop-up messages, and fake security software are just a few examples of the deceptive methods used to trick users into paying for unnecessary services or providing access to their personal information. As technology advances, it is crucial for users to stay vigilant, be aware of these scams, and adopt best practices to protect themselves from falling victim to such fraudulent activities.
Investment Scams
Investment scams have been a persistent threat to investors, exploiting their desire for quick and substantial returns. Among the various fraudulent schemes, three particularly notorious ones are Ponzi Schemes, Pump and Dump, and Binary Options Fraud.
1. Ponzi Schemes:
One of the oldest and most infamous investment scams is the Ponzi Scheme, named after Charles Ponzi, who orchestrated one of the earliest recorded schemes in the early 20th century. Typically, a Ponzi Scheme involves an individual or entity promising high returns with little to no risk to investors. The returns are paid using the capital from new investors, creating the illusion of a profitable enterprise. An example of a Ponzi Scheme unfolded in the early 2000s with the case of Bernie Madoff. His investment firm, Bernard L. Madoff Investment Securities LLC, defrauded thousands of investors, claiming consistent high returns. Madoff’s scheme collapsed in December 2008, revealing losses amounting to billions of dollars. Madoff was sentenced to 150 years in prison in 2009 for orchestrating one of the largest Ponzi schemes in history.
2. Pump and Dump:
Pump and Dump schemes involve artificially inflating the price of a stock or security through false or misleading information, only to sell off the overvalued asset at a profit. This fraudulent practice often targets unsuspecting investors who buy into the hype surrounding a particular investment. In the early 2000s, the “Wolf of Wall Street,” Jordan Belfort, was involved in a Pump and Dump scheme. Belfort’s brokerage firm, Stratton Oakmont, manipulated the prices of various stocks, leading to significant losses for investors. Belfort pleaded guilty to fraud and related crimes, serving prison time and being ordered to pay restitution to the defrauded investors.
3. Binary Options Fraud:
Binary options fraud gained prominence in the mid-2010s, exploiting the simplicity of binary options trading. In binary options, investors bet on whether the price of an asset will rise or fall within a specified timeframe. Fraudulent brokers manipulate the outcome, making it nearly impossible for investors to profit. One notable case involves the binary options scheme orchestrated by Yukom Communications Ltd. and its owner, Lee Elbaz. In 2019, Elbaz was convicted in the United States for her role in defrauding investors through the manipulation of binary options. The scheme defrauded investors of tens of millions of dollars, emphasizing the need for increased regulatory scrutiny in the binary options industry.
Investors must remain vigilant and informed to protect themselves from falling victim to these investment scams. Regulatory bodies and law enforcement agencies play a crucial role in investigating and prosecuting individuals involved in fraudulent schemes, but awareness and education are equally essential to prevent financial devastation. As financial markets evolve, so do the tactics of fraudsters, making it imperative for investors to stay informed and exercise caution when approached with investment opportunities that seem too good to be true.
Ransomware Attacks
1. Definition: Ransomware is a type of malicious software that encrypts a victim’s files or system, rendering them inaccessible. The attacker then demands a ransom, usually in cryptocurrency, in exchange for the decryption key. This form of cybercrime has become increasingly prevalent in recent years, posing a significant threat to individuals, businesses, and even critical infrastructure.
2. Common Targets: Ransomware attacks can target a wide range of entities, from individuals to large corporations and government organizations. One common target is the healthcare sector, as seen in the infamous WannaCry attack in May 2017. This global cyber assault affected over 200,000 computers across 150 countries, encrypting data and demanding bitcoin payments. Hospitals and healthcare facilities were particularly vulnerable, impacting patient care and highlighting the life-threatening consequences of ransomware. Another common target is the financial sector, where attacks can disrupt operations and compromise sensitive customer data. In 2020, the Maze ransomware group targeted various financial institutions, exposing the vulnerability of critical infrastructure to these cyber threats. The attackers not only demanded payment for decryption but also threatened to release sensitive information if the ransom was not paid, adding an additional layer of extortion. Small and medium-sized enterprises (SMEs) are also frequent victims of ransomware attacks due to potentially weaker cybersecurity measures. The prevalence of attacks on smaller businesses is exemplified by the Ryuk ransomware, which emerged in 2018. Ryuk has targeted various organizations worldwide, encrypting files and demanding significant ransom payments. Its success lies in its ability to adapt and target organizations with specific vulnerabilities, regardless of their size.
3. Prevention: Preventing ransomware attacks requires a multifaceted approach that combines technological measures, user awareness, and proactive cybersecurity practices.
- Regular Backups: Regularly backing up critical data is essential to mitigating the impact of a ransomware attack. Backups should be stored offline or in a secure, isolated environment to prevent them from being compromised.
- Security Software: Employing robust antivirus and anti-malware software can help detect and prevent ransomware infections. Keeping security software up to date ensures that it can effectively identify and block emerging threats.
- Employee Training: Human error is a common entry point for ransomware attacks. Educating employees about phishing emails, suspicious links, and other social engineering tactics can significantly reduce the risk of infection.
- Patch Management: Keeping operating systems and software up to date with the latest security patches is crucial. Many ransomware attacks exploit known vulnerabilities, and timely updates can close these entry points.
- Network Segmentation: Restricting access within a network through segmentation can limit the spread of ransomware. If one segment is compromised, it minimizes the potential impact on the entire network.
- Incident Response Plan: Developing and regularly testing an incident response plan ensures a swift and coordinated reaction in the event of a ransomware attack. This includes isolating affected systems, notifying authorities, and initiating the recovery process.
Ransomware attacks continue to evolve, posing an ongoing threat to individuals, businesses, and critical infrastructure. Staying vigilant, implementing proactive security measures, and fostering a cybersecurity-aware culture are essential steps in mitigating the risk and impact of these malicious attacks.
Social Media Scams
In the digital age, where the virtual realm seamlessly integrates with our daily lives, social media has become a breeding ground for scams that exploit the trust and vulnerabilities of unsuspecting users. From fake profiles to sophisticated social engineering tactics, these scams continue to evolve, posing significant threats to individuals and businesses alike.
1. Fake Profiles: A Web of Deception
One prevalent form of social media scam involves the creation of fake profiles. These impostors weave intricate tales to lure users into their web of deception, often preying on emotions or exploiting personal information. Dating back to the early days of social media, fake profiles have evolved in complexity and scale. Take, for example, the notorious “Catfish” phenomenon that gained prominence in the mid-2010s. The term, popularized by the MTV show of the same name, refers to individuals creating deceptive online personas to engage in fraudulent relationships. In one high-profile case from 2014, Notre Dame football player Manti Te’o fell victim to a fake girlfriend who never existed. This incident highlighted the emotional toll and potential reputational damage associated with fake profiles. As technology advances, so do the tactics of those behind fake profiles. In recent years, the rise of deepfake technology has allowed scammers to manipulate audio and video, further blurring the lines between reality and fiction. These deceptive profiles can be used for identity theft, financial fraud, or even to spread disinformation.
2. Social Engineering: The Art of Manipulation
Social engineering is another potent weapon in the arsenal of social media scammers. By exploiting psychological and emotional triggers, these attackers manipulate individuals into divulging sensitive information or taking actions they otherwise wouldn’t. In 2016, a phishing scam targeted Gmail users, attempting to trick them into revealing their login credentials. The scam, disguised as a Google Docs invitation, spread rapidly through social media. Users who clicked the link unwittingly granted access to their Gmail accounts, allowing the attackers to compromise personal and professional information. This incident underscores the effectiveness of social engineering in leveraging trust to achieve malicious objectives.
3. Fake Contests and Giveaways: A Mirage of Rewards
Fake contests and giveaways are yet another facet of social media scams, preying on users’ desire for recognition and rewards. Scammers create enticing contests or giveaways that promise lucrative prizes, ranging from cash and gadgets to exclusive experiences. In reality, these are elaborate schemes to harvest personal information, such as email addresses, phone numbers, or even financial details. In 2020, during the height of the COVID-19 pandemic, scammers exploited people’s vulnerabilities by posing as organizations offering relief funds or giveaways. These deceptive campaigns capitalized on the uncertainty and economic challenges, leading many unsuspecting individuals to fall victim to identity theft or financial scams.
The landscape of social media scams is ever-evolving, demanding increased awareness and vigilance from users. Fake profiles, social engineering tactics, and deceptive contests are just a few examples of the myriad strategies employed by scammers to exploit the digital realm. Staying informed, practicing skepticism, and adopting robust security measures are crucial in safeguarding against the shadowy threats that lurk in the interconnected world of social media.
Job and Employment Scams
In the fast-paced and competitive world of job hunting, individuals are often eager to secure employment opportunities quickly. Unfortunately, this urgency can make them vulnerable to various job and employment scams. These scams come in different forms, preying on the desperation of job seekers. Here, we’ll delve into three common types of job scams—Fake Job Offers, Pyramid Schemes, and Work-from-Home Scams—each with its own set of red flags.
1. Fake Job Offers:
Fake job offers have become increasingly sophisticated, with scammers creating authentic-looking job postings and websites to lure unsuspecting victims. This scam often involves individuals posing as recruiters or hiring managers from legitimate companies. They may conduct fake interviews and request personal information, such as Social Security numbers or bank details. One notable case occurred in March 2023 when a fake tech company advertised high-paying remote positions. Job seekers who applied were subjected to an elaborate interview process, only to find out later that the company did not exist. To avoid falling victim to such scams, it’s crucial to research the company thoroughly, check for official communication channels, and never share sensitive information without proper verification.
2. Pyramid Schemes:
Pyramid schemes disguise themselves as legitimate business opportunities but operate on a recruitment-based model rather than product sales. In a pyramid scheme, participants are promised high returns for recruiting others, creating a hierarchical structure that ultimately leaves those at the bottom with financial losses. In September 2023, a notable pyramid scheme disguised as a marketing agency promising lucrative income opportunities gained traction on social media platforms. Victims were required to invest money upfront and recruit others to do the same. However, the scheme collapsed, leaving many without the promised returns. It’s essential to be wary of opportunities that require substantial upfront investments or focus heavily on recruitment, as these are indicative of pyramid schemes.
3. Work-from-Home Scams:
The rise of remote work has opened the door for scammers to exploit individuals seeking flexible employment options. Work-from-home scams often involve fraudulent companies offering easy, high-paying jobs with minimal effort. These scams may require an initial payment for training materials or software, only to disappear once the payment is made. A notable case in January 2024 involved a fake data entry company that claimed to provide remote jobs with substantial salaries. Job seekers were required to pay a fee for access to a specialized data entry software, only to discover that the software was non-existent, and the company vanished with their money. To avoid falling for work-from-home scams, individuals should be cautious of job offers that sound too good to be true, conduct thorough research on the company, and never pay upfront fees for employment opportunities.
Job and employment scams continue to evolve, becoming more sophisticated and harder to detect. It is crucial for job seekers to remain vigilant, conduct thorough research, and trust their instincts. By being aware of the red flags associated with fake job offers, pyramid schemes, and work-from-home scams, individuals can protect themselves from falling victim to these deceptive practices in the ever-changing landscape of the job market.
Mobile App Scams
In the rapidly evolving landscape of technology, mobile applications have become an integral part of our daily lives, providing convenience, entertainment, and connectivity. However, with the proliferation of mobile apps, there has been a parallel increase in mobile app scams, exploiting unsuspecting users and posing significant threats to their privacy and security. Here, we delve into three prevalent forms of mobile app scams: malicious apps, fake banking apps, and SMS phishing (smishing).
1.Malicious Apps:
Malicious apps represent one of the most insidious threats in the realm of mobile app scams. Cybercriminals often disguise these apps as legitimate and useful applications, enticing users to download and install them. Once installed, these malicious apps can compromise sensitive information, such as login credentials, personal data, and even financial details. A notable incident occurred in September 2022 when a popular productivity app was compromised by hackers, leading to a massive data breach affecting millions of users. The attackers exploited vulnerabilities in the app’s security, gaining unauthorized access to user accounts and harvesting a trove of personal information. Users were advised to update their apps and change their passwords promptly. To safeguard against such threats, users are encouraged to download apps only from official app stores, regularly update their apps, and scrutinize app permissions before installation.
2. Fake Banking Apps:
The rise of digital banking has brought about a surge in fake banking apps designed to mimic legitimate financial institutions. These deceptive apps aim to trick users into divulging sensitive banking information, such as account numbers and passwords, by imitating the appearance and functionality of authentic banking apps. In February 2023, a wave of fake banking apps emerged, targeting customers of a prominent bank. These apps, available on third-party app stores, claimed to offer enhanced security features and promotions. Unwitting users who installed these counterfeit apps inadvertently exposed their banking credentials, leading to unauthorized transactions and financial losses. To avoid falling victim to fake banking apps, users should only download financial applications from official app stores, verify the legitimacy of the app and its developer, and regularly monitor their bank accounts for any suspicious activities.
3. SMS Phishing (Smishing):
SMS phishing, commonly known as smishing, involves the use of text messages to trick users into divulging personal information or clicking on malicious links. In June 2023, a widespread smishing campaign targeted mobile users, claiming to be from a well-known online retailer and promising exclusive discounts. The messages contained links that, when clicked, led users to phishing websites designed to harvest login credentials and credit card information. Users should exercise caution when receiving unexpected messages, especially those containing links or requesting personal information. Authentic organizations typically do not request sensitive information via text messages. The threat landscape for mobile app scams is dynamic and ever-evolving. To mitigate risks, users must remain vigilant, adopt best practices such as downloading apps from official stores, and stay informed about emerging threats. As technology continues to advance, so too must our awareness and diligence in safeguarding our digital lives against the perils of mobile app scams.
Cryptocurrency Scams
Cryptocurrency, a revolutionary and decentralized form of digital currency, has gained popularity in recent years. However, the rise of cryptocurrencies has also given rise to a darker side of the industry – cryptocurrency scams. These scams exploit the decentralized and pseudonymous nature of cryptocurrencies, making it challenging for regulators to track and prosecute perpetrators. Here, we delve into three common types of cryptocurrency scams: Initial Coin Offerings (ICOs), Pump and Dump Schemes, and Fake Wallets and Exchanges.
1. Initial Coin Offerings (ICOs): ICOs are a fundraising method wherein new cryptocurrencies are offered to the public in exchange for existing cryptocurrencies or fiat money. While legitimate ICOs serve as a means for new projects to secure funding, fraudulent ones have plagued the industry. One notorious example is the case of Centra Tech in 2017. The company claimed to offer a debit card backed by Visa and Mastercard, but it was later revealed that the founders had fabricated partnerships and misled investors. The U.S. Securities and Exchange Commission (SEC) filed charges against Centra Tech, leading to the arrest of the founders and the return of millions of dollars to defrauded investors.
2. Pump and Dump Schemes: Pump and dump schemes involve artificially inflating the price of a cryptocurrency through false or misleading statements, only for the orchestrators to sell their holdings at the inflated prices. In 2018, the SEC took action against a group of individuals behind the “Centra Coin” pump and dump scheme. The organizers used social media and other online platforms to spread false information about the cryptocurrency, enticing investors to buy in. Once the price surged, the perpetrators sold their holdings, leaving unsuspecting investors with significant losses. The SEC charged the individuals with fraud, emphasizing the need for investors to remain vigilant against such schemes.
3. Fake Wallets and Exchanges: The proliferation of cryptocurrencies has led to an influx of wallet and exchange platforms, providing ample opportunities for scammers to create fake ones. These fraudulent wallets and exchanges often mimic legitimate services, luring users to deposit their funds. One notable example is the case of My Big Coin in 2017. The company claimed to offer a secure cryptocurrency wallet and exchange but was later revealed to be a Ponzi scheme. The founders were charged with fraud, and the CFTC (Commodity Futures Trading Commission) secured a court order to shut down the operation.
Investors and enthusiasts must exercise caution and conduct thorough research before participating in any ICOs, investing in cryptocurrencies, or using new wallets and exchanges. Regulatory bodies worldwide are working to establish guidelines and crackdown on fraudulent activities, but due diligence remains the responsibility of individual investors.
While cryptocurrencies hold immense potential, the prevalence of scams underscores the importance of a vigilant and informed community. By staying informed about the risks associated with ICOs, pump and dump schemes, and fake wallets/exchanges, investors can navigate the cryptocurrency landscape more safely and contribute to the long-term sustainability and legitimacy of this
Child Exploitation Scams
Child exploitation scams have become a disturbingly prevalent issue in today’s digital age, targeting vulnerable children through various means. Online predators, sextortion, and the overall safety of children on the internet are critical aspects of this dark reality.
1. Online Predators: Online predators use the anonymity provided by the internet to exploit children. They often pose as peers or authority figures to gain the trust of their victims. One notorious case is that of Mark Andrew Twitchell in 2008. He used online platforms to lure a young man, ultimately leading to a heinous crime. This incident underscored the importance of vigilance and education to protect children from falling prey to such predators. The rise of social media platforms has provided new avenues for predators. Cases of individuals befriending minors on platforms like Facebook, Instagram, or Snapchat, pretending to be someone they are not, have become alarmingly common. As technology advances, so do the tactics of these predators, making it crucial for parents and guardians to stay informed and engaged in their children’s online activities.
2. Sextortion: Sextortion involves manipulating victims, often minors, into providing explicit images or videos, followed by threats of exposure unless further explicit content or actions are provided. In 2017, the “Blue Whale Challenge” gained notoriety, where victims, primarily adolescents, were coerced into completing a series of harmful tasks, including sharing explicit material. This chilling example illustrates the dark and manipulative nature of sextortion schemes. Perpetrators may use the compromising material to extort money or control the victim. Awareness campaigns and education about responsible online behavior are crucial to combatting sextortion. Empowering children with the knowledge to recognize and report such incidents is a key step in preventing further harm.
3. Protecting Children Online: Safeguarding children from online exploitation requires a multi-faceted approach involving parents, educators, law enforcement, and the technology industry. A significant step is fostering open communication with children about the potential dangers they may encounter online. Encouraging them to share their online experiences can help identify red flags and intervene before any harm occurs. Parents should establish guidelines for internet use, including the importance of privacy settings, the danger of sharing personal information, and the potential risks of interacting with strangers online. Schools play a crucial role by integrating digital literacy and online safety education into their curriculum. Technology companies also bear responsibility by implementing stringent measures to identify and remove harmful content, as well as developing tools to track and report suspicious activities. Collaboration between these stakeholders is essential to create a safer online environment for children.
Child exploitation scams manifest in various forms, ranging from online predators to sextortion schemes. Vigilance, education, and open communication are pivotal in protecting children from falling victim to these malicious activities. By staying informed and actively engaging in the online lives of children, we can collectively work towards a safer digital landscape for the younger generation.
Government Impersonation Scams
Government impersonation scams have become increasingly prevalent in recent years, exploiting people’s trust in official institutions to trick them into divulging sensitive information or parting with their hard-earned money. Three common types of government impersonation scams include IRS scams, law enforcement impersonation, and utility scams.
1. IRS Scams: One notorious form of government impersonation scam involves individuals posing as representatives of the Internal Revenue Service (IRS). Typically, victims receive intimidating phone calls or emails claiming that they owe back taxes and threatening legal action or arrest if immediate payment is not made. The scammers often manipulate caller ID information to appear as if the call is coming from the IRS. In a prominent case in 2018, a wave of IRS scams swept across the United States. Callers would assert that the target owed unpaid taxes and demanded immediate payment via wire transfer or prepaid debit cards. The scammers often used aggressive and threatening language to create a sense of urgency. To combat such scams, the IRS repeatedly emphasized that it does not initiate contact with taxpayers by phone, and individuals should be cautious and verify the legitimacy of any communication claiming to be from the IRS.
2. Law Enforcement Impersonation: Law enforcement impersonation scams involve fraudsters posing as police officers or other law enforcement officials to exploit individuals’ fear and respect for authority. These scams may take various forms, such as phone calls, emails, or even in-person visits. The scammers may claim that the victim has outstanding warrants, owes fines, or is involved in illegal activities. In a notable case in 2019, individuals posing as police officers called victims in the United Kingdom, claiming to be from the Metropolitan Police. The scammers convinced victims that their bank accounts were compromised and instructed them to transfer funds to a “safe” account. The impersonation of law enforcement added an extra layer of credibility to the scam, making victims more likely to comply. Law enforcement agencies worldwide consistently remind the public that they do not make unsolicited calls demanding money or personal information.
3. Utility Scams: Utility scams involve impostors posing as representatives from utility companies, such as electricity, gas, or water providers. These scammers often target businesses and individuals, threatening service disconnection unless an immediate payment is made. They may request payment via prepaid debit cards, wire transfers, or cryptocurrency. In 2020, during the COVID-19 pandemic, there was a surge in utility scams across various countries. Scammers took advantage of the increased vulnerability and financial stress caused by the pandemic to exploit individuals and businesses. Utility companies consistently remind customers that they do not demand immediate payment or threaten disconnection without prior notice.
Government impersonation scams continue to pose a significant threat to individuals and businesses worldwide. The key to avoiding falling victim to these scams is to remain vigilant, verify the legitimacy of any unexpected communication, and never provide personal or financial information to unsolicited contacts. Governments and law enforcement agencies also play a crucial role in raising awareness and providing guidance to the public to help them recognize and report these scams promptly.
Conclusion
Internet scams pose a pervasive and evolving threat to individuals and businesses alike. The rapid expansion of online connectivity has facilitated a breeding ground for a variety of deceptive practices, ranging from phishing schemes and identity theft to more sophisticated cybercrimes. As technology advances, so do the tactics employed by cybercriminals, making it imperative for users to remain vigilant and adopt robust cybersecurity measures. The financial implications of falling victim to internet scams can be severe, causing substantial economic losses and emotional distress. Governments, law enforcement agencies, and cybersecurity experts must collaborate to enhance preventative measures, enforce stricter regulations, and prosecute offenders to deter such illicit activities. Additionally, public awareness campaigns are crucial to educating individuals about the various forms of internet scams and empowering them to recognize and avoid potential threats. Ultimately, combating internet scams requires a collective effort, involving a combination of technological innovation, legal measures, and proactive user engagement. As we navigate the ever-expanding digital landscape, a heightened awareness of online risks and a commitment to cybersecurity best practices are essential to safeguarding individuals and organizations from the detrimental impacts of internet scams.






Leave a Reply